THM Sakura Room Write-up
I came across this CTF as part of my journey into OSINT, and decided to give it a go.
This had been the most advanced OSINT I had found so far, and it was a welcome challenge. I really enjoyed the different tests and how I had to make use of different skills in order to get through it.
And this is how I went about it…
Task 1 - Introduction to the Room
Task 2 - Finding the Attacker’s Username
We are tasked with finding the attacker’s username. We are told that the forensic analysis team found an image that was left behind by the attacker. We should take a closer look a it in the link they provide us.
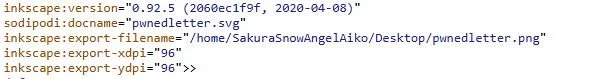
The image in on itself doesn’t give us much information. The binary code in the back didn’t reveal the information I needed. Instead, I viewed the source code of this website and found the metadata of the image.
Here we can clearly see the attackers username as part of the image’s directory
Task 2 Answers
What username does the attacker go by?
Answer: SakuraSnowAngelAiko
Task 3 - Finding the Attacker’s Email Address
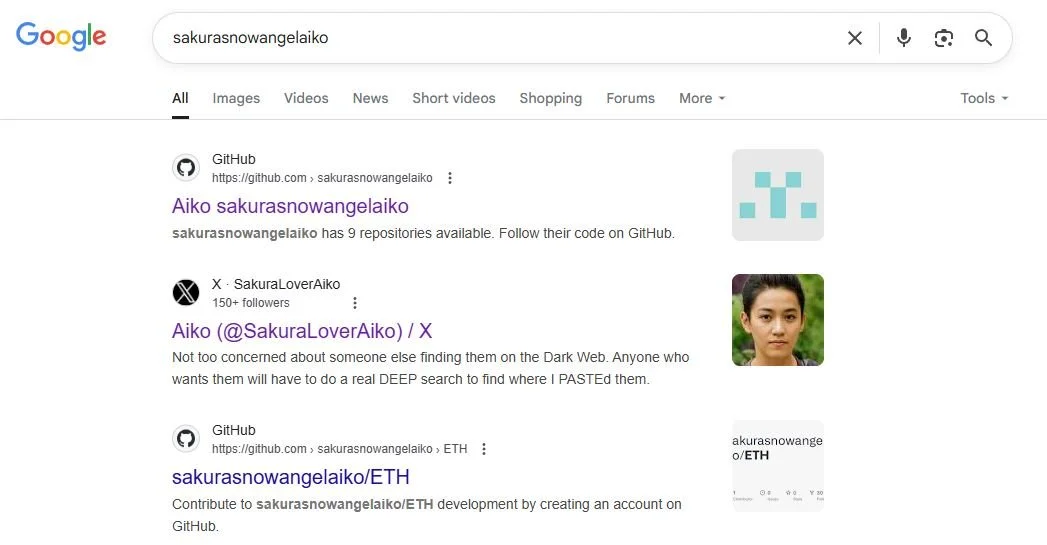
Since I obtained the attacker’s username, I could now make a simple google search to find out more about the target.
We find some interesting profiles for this user.
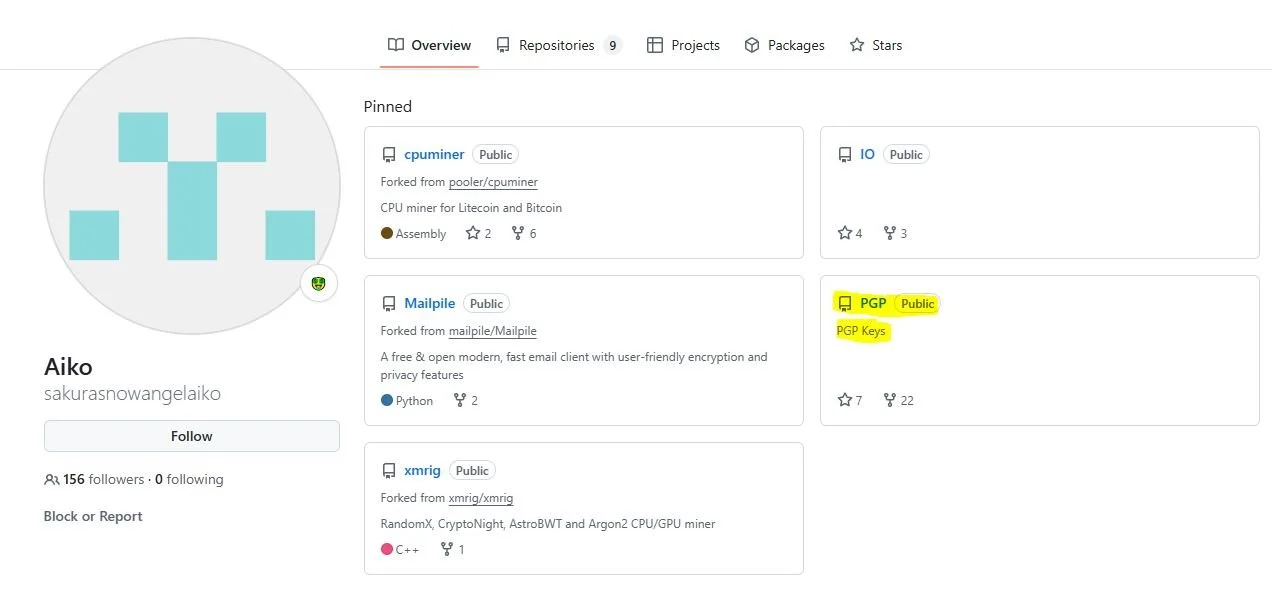
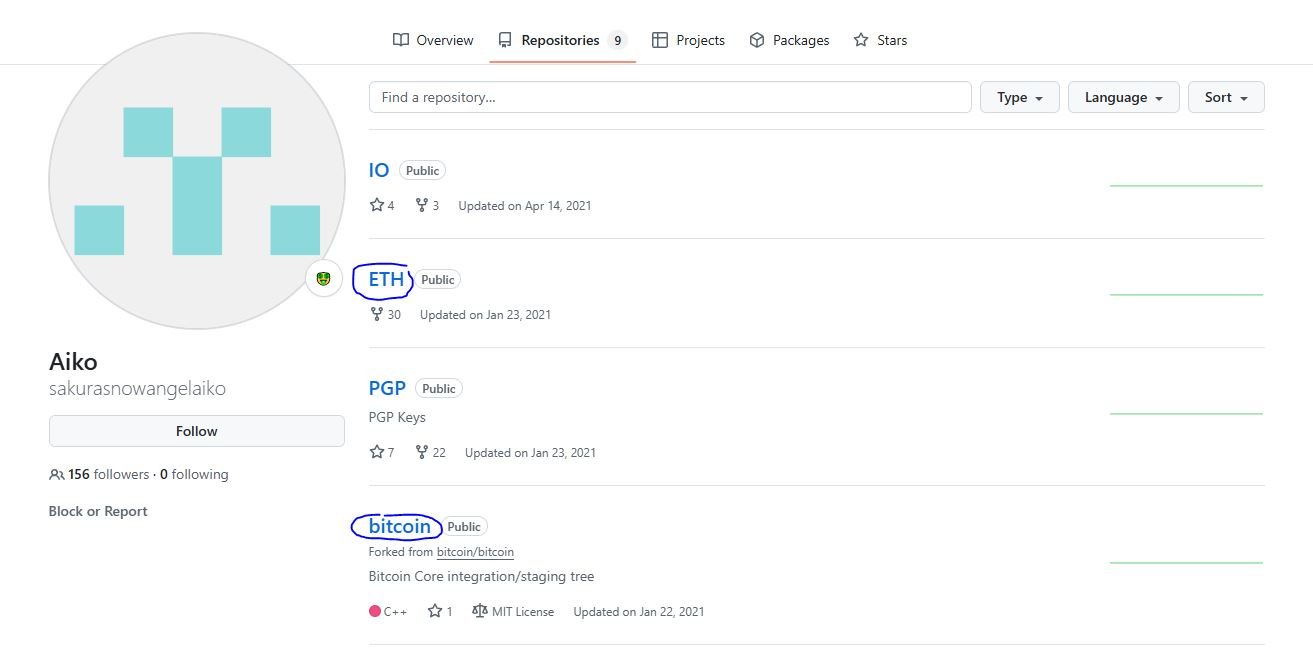
I checked the GitHub first. This repo called PGP keys looked promising. PGP is a popular encryption program used to secure email communications, files, and other data. Not really something you should be sharing on your very public profile!
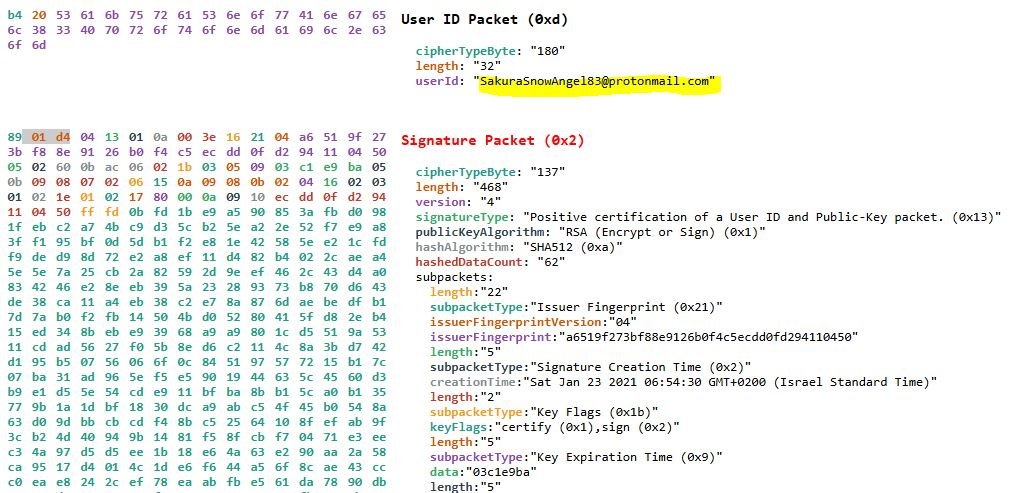
I got the PGP key, now what? I ran it through https://cirw.in/gpg-decoder/ which is a tool that helps in decoding these types of keys. This gives us the user’s email
Task 3 Answers:
Name: Aiko Abe (from LinkedIn and Twitter)
Email: SakuraSnowAngel83@protonmail.com
Task 4 - What cryptocurrency does the attacker own a cryptocurrency wallet for?
This was where I started to feel a bit more challenged, since I’m not all that familiar with cryptocurrency. According to the THM room, we should check the GitHub and the commit histories in order to get more information. The first repo to catch my attention was the bitcoin one, since it’s the most known cryptocurrency. I explored it, but didn’t really find anything that would give me further information into their crypto wallet. I googled the other names, IO and ETH, and found that ETH stands for “Ethereum”, which is another type of cryptocurrency.
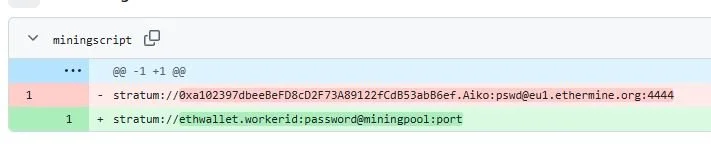
Inside of the ETH repo, I found only two strings, but they already seemed more promising with one having the word “wallet” in it, and even an id? I looked further into this by googling the strings. and came across a website called https://etherscan.io/ and learned that
0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6ef
was the wallet address with which we can see the transaction history of this wallet. With this, we can answer the rest of the questions for this task.
Task 4 Answers
What cryptocurrency does the attacker own a cryptocurrency wallet for?
Ethereum
What is the attacker's cryptocurrency wallet address?
0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6ef
What mining pool did the attacker receive payments from on January 23, 2021 UTC?
Ethermine
What other cryptocurrency did the attacker exchange with using their cryptocurrency wallet?
Tether
Task 5 - TAUNT
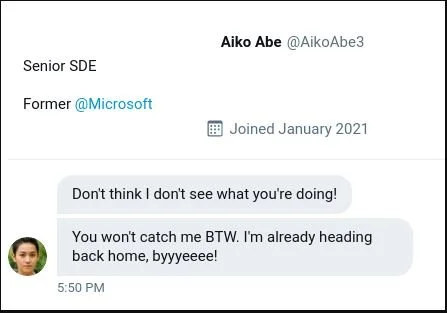
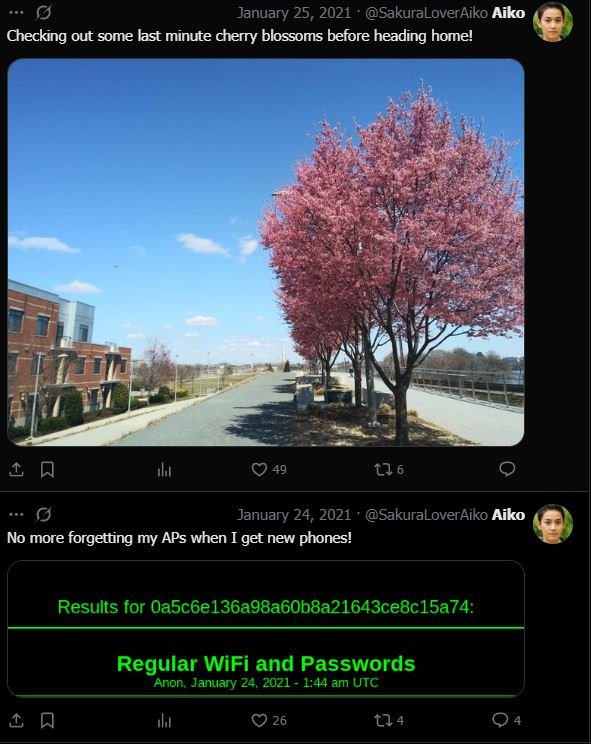
It seems that the attacker is taunting us from a twitter account with a different handle. This is the image we are given:
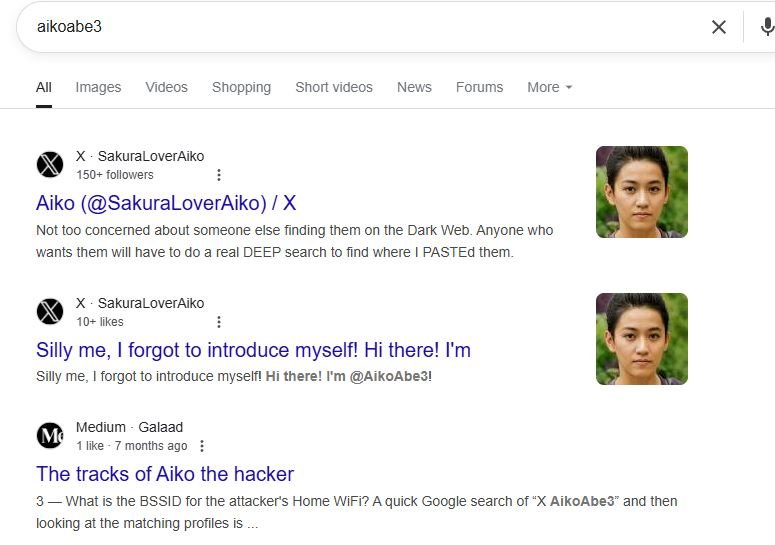
I found this twitter profile through a quick google search and we can see that the new twitter handle is SakuraLover
I look a look at their twitter profile. Right off the bat, I found some interesting things. First off, a picture of the last place the attacker visited. Is that the Washington Monument way off in the back?
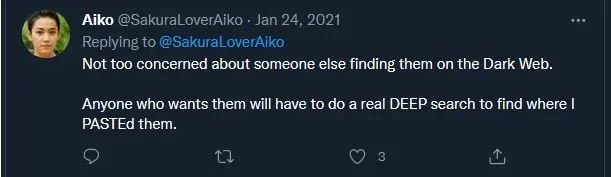
And secondly, this post about APs which apparently they stored in a Dark Web site.
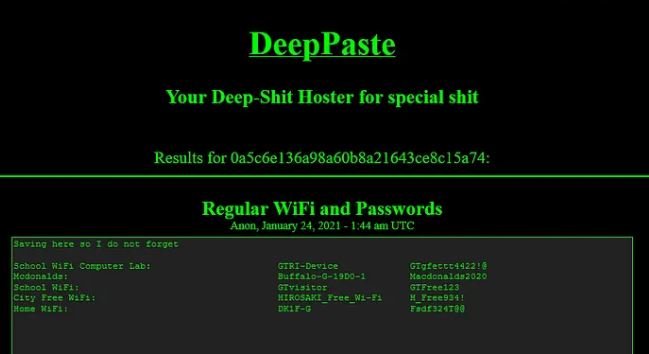
Off to the Dark Web I went. I searched for sites that might be related to “Deep search”, “Deep Paste”, “Search Paste” etc. Based off on the attacker’s hints. I came across Deep Paste, which allows users to paste any text they want into the site. I looked up the Hash from Aiko’s tweet: “0a5c6e136a98a60b8a21643ce8c15a74” and got the information I was looking for.
Great! I got more information. THM is asking for the BSSID, which we can find by using https://wigle.net/ , which is a tool specific for looking up BSSIDs or SSIDs. I used a free account and searched for the attacker’s home SSID, which turned up a city in Japan and their BSSID.
Task 5 Answers
What is the attacker's current Twitter handle?
SakuraLoverAiko
What is the BSSID for the attacker's Home WiFi?
84:af:ec:34:fc:f8
Task 6 -Homebound
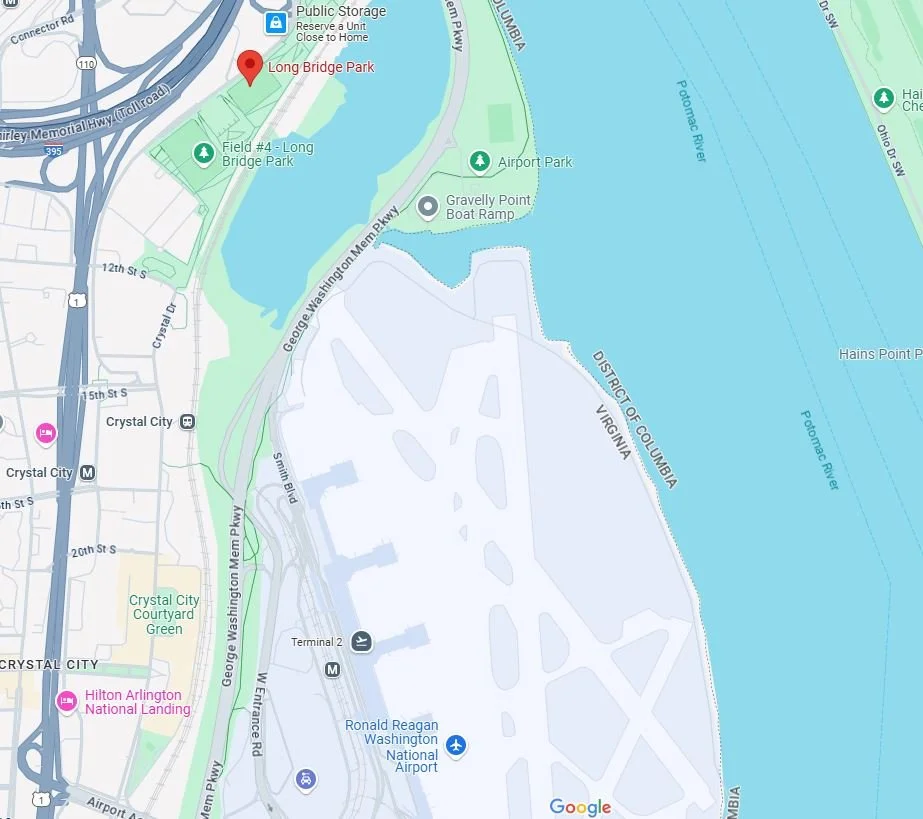
Here, we are asked to find the attacker’s last location and home by using OSINT techniques. I had already noticed the Washington Monument in the background of their tweet, so I dug a bit deeper to confirm. I google reverse searched the picture, avoiding the cherry blossom tree, in order to get more accurate results. I found a picture on flickr that looks taken from about the same angle, but a different season! I checked the name of the album for this picture and it says “Long Bridge Park” in Arlington, Virginia.
Seems like a pretty close match! THM is asking which is the closet airport to this location shared by the attacker. By searching the park on google maps and zooming out just a little bit, I found that there’s an airport pretty close by! The Ronald Reagan Washington National Airport.
Next, we are asked where they stopped for a Layover. The attacker posted an image of the lounge they visited during they layover. So I could easily google for JAL’s First Class Lounge -Sakura Lounge. Through Jal’s website, I found that this lounge is located in Tokyo International Airport (Haneda)
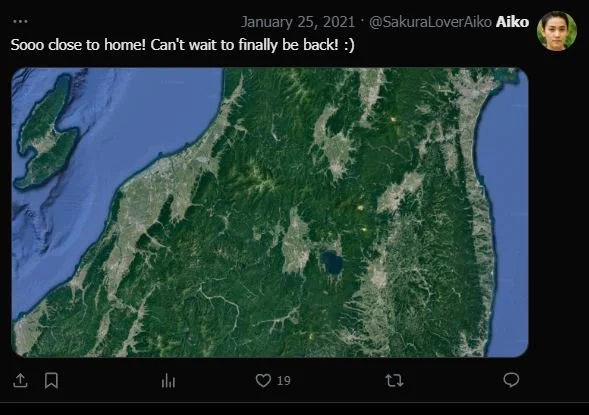
And finally, we are asked which Lake can be seen in the map shared by the attacker, and which city does the attacker call home. Luckily for us, the attacker likes to share a lot of information on their twitter.
Using Google Lens, I got results for the Yamagata prefecture, which I then searched for in google maps with satellite view. It was a perfect match, and I found that the lake is called Lake Inawashiro. As to the attacker’s home, we got this information back when we were searching for their BSSID, we can see City Wi-fi: “Hirosaki Free Wi-fi”. So there you have it.
Task 6 Answers:
What airport is closest to the location the attacker shared a photo from prior to getting on their flight?
DCA
What airport did the attacker have their last layover in?
HND
What lake can be seen in the map shared by the attacker as they were on their final flight home?
Lake Inawashiro
What city does the attacker likely consider "home"?
Hirosaki